1. Getting Started with Python
Welcome to the Python for Cybersecurity web course!
Wondering why specific focus is being given to cybersecurity or why should you bother? Well, the answer is pretty simple.
“You are only secure until you believe you are secure.

Not making much sense, is it? In simple words, there is nothing secure in the internet — This is the bitter truth!
If someone says otherwise, do not believe them.
In most cases, much emphasis does not go into the security aspect of developing any product, solution or application, which backfires on the organization involved, when someone finally gains control of their resources and network through some simple vulnerability that existed. With the realization dawning on most of the organizations and companies, from startups to tech giants, all have started to emphasize on the importance of security. Thus cybersecurity has become one of the most in-demand fields.
Ever seen the following map before?
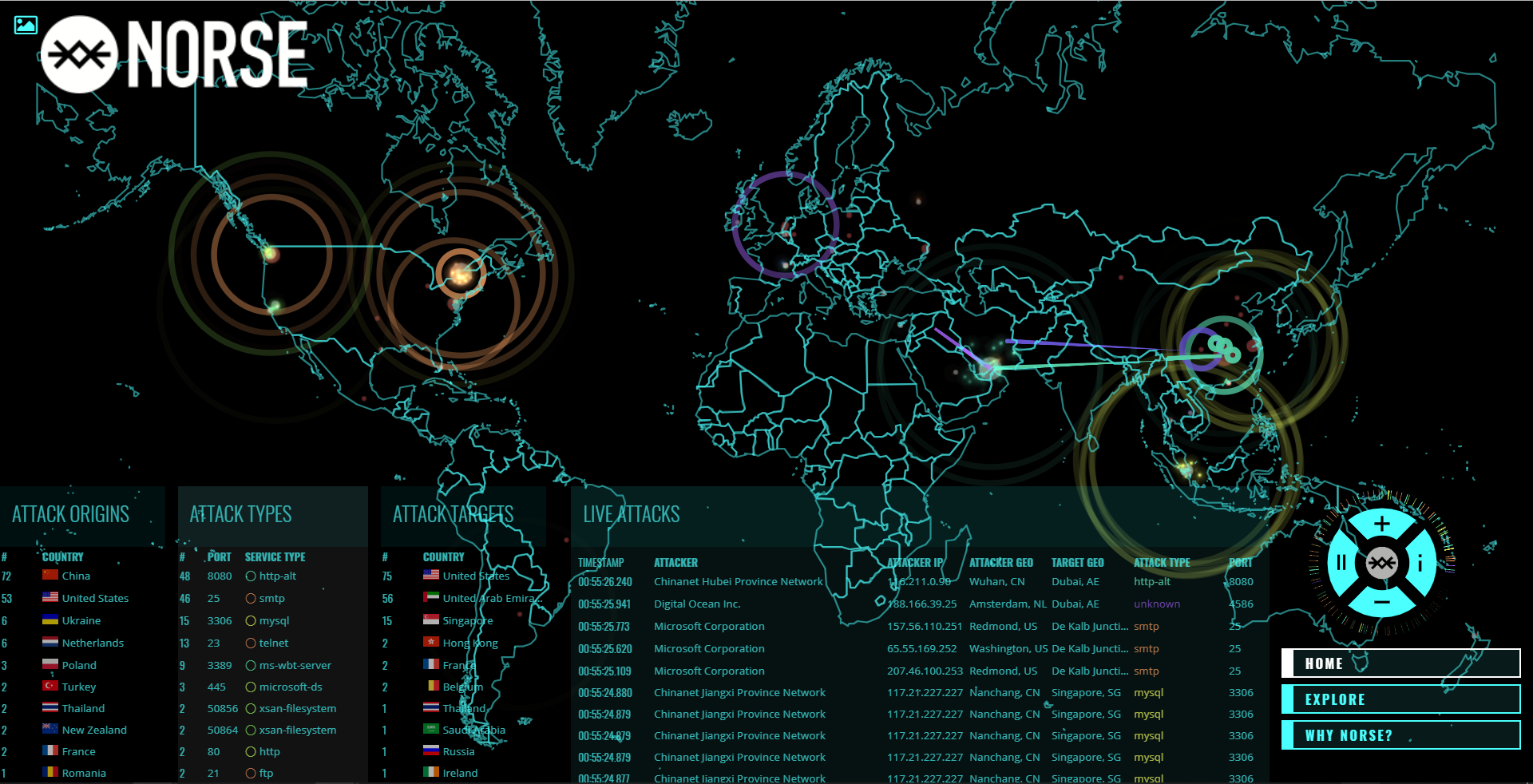
This live map in the norsecorp website gives you real-time information of which countries are currently being cyber-attacked! This is just one of those avenues to understand how the importance of enhancing cybersecurity in everything we build is the need of the hour — rather, need of the minute!
Now that we have made a little sense of why cybersecurity is important, let us dive into our first lesson!
In this lesson, we will learn about why Python is one of the most in-demand skills among cybersecurity recruits and also try to learn and understand the fundamentals of the language.
But, why Python for Cybersecurity?
It doesn’t come as a surprise that Python is one of the most sought-after programming languages for cybersecurity considering its:
Extensive library of powerful packages that supports Rapid Application Development (RAD)
Clean syntax code and modular design
Automatic memory management and dynamic typing capability
Mixed code environments to combine different programming languages (MicroPython, Cython, Jython, Skulpt (JS), PyPy)
Source: makromikro.me

Everything from testing microchips at Intel, to powering Instagram, to building video games with PyGame, Python is the most sought after programming language for its power packed capabilities.
With that being said, let us dive into the first lesson of our Python for Cyber Security course — Introduction to Python!
Learning Goals
Getting familiar with the basics datatypes, structures, syntax and constructs of the Python programming language.
Code walk-through of how each of these are declared and implemented.
Estimated time to complete : 1 hour.
Environment Setup
To get started, ensure that your system has the following requirements fulfilled:
Install Python 3.4 or higher.
You can use any of the IDEs and Editors available (IDLE, PyCharm, Jupyter Notebook, Spyder, Thonny, PyDev for Eclipse, Sublime Text, Notepad++, NetBeans, Komodo, Atom, etc)
I will be using Jupyter Notebook predominantly throughout this course for the coding examples in Python.Source: https://www.deviantart.com/cryptid-creations

Basics of Python programming
In this section, we will be covering the basics of the Python programming language including the syntax and usage of:
Variable Names
Functions
Numbers and Operators
Loops and Statements
String functions
File functions
Data Structures
Regular Expressions
Let’s roll!Source: launchacademy.com
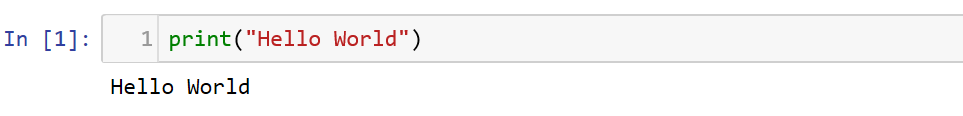
Just like how any programming language introduction begins in this world, let us print “Hello World”.
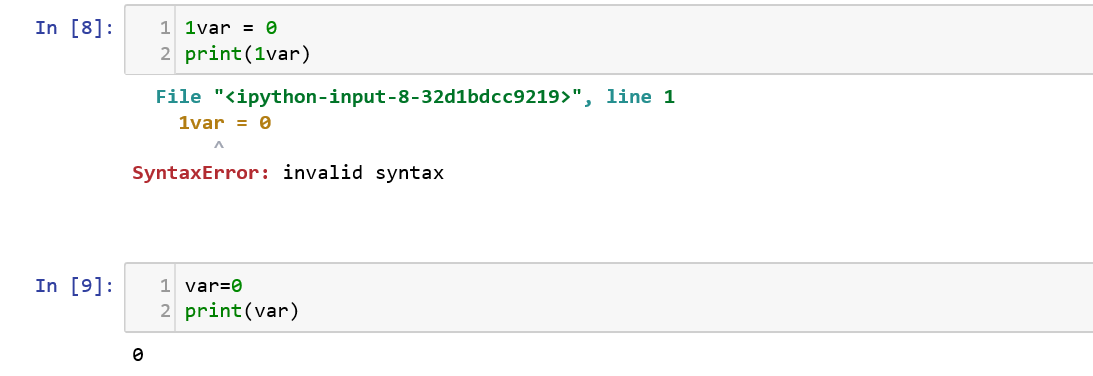
Variable Names
There are a few rules that needs to be followed when it comes to naming variables in Python:
Names can not start with a number.
There can be no spaces in the name, use _ instead.
Can’t use any of these symbols :’”,<>/?|\()!@#$%^&*~-+
It’s considered best practice (PEP8) that names are lowercase.
Avoid using the characters ‘l’ (lowercase letter el), ‘O’ (uppercase letter oh), or ‘I’ (uppercase letter eye) as single character variable names.
Avoid using words that have special meaning in Python like “list” and “str”
Functions
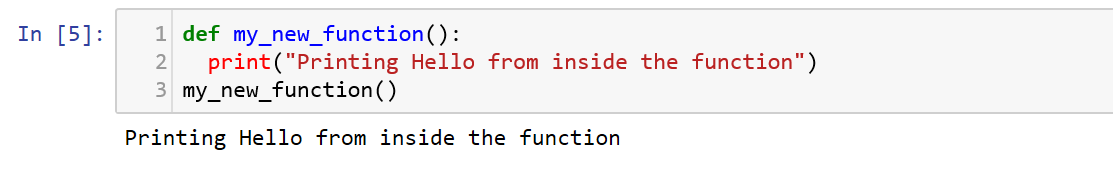
In Python, a function declaration begins with the keyword “def” for defining the function and ends with “:” marking the end of the declaration. In the example, we declare a function called my_new_function().
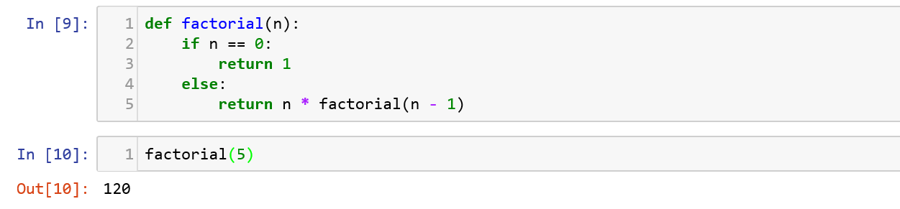
Recursion
A recursive function is the one which calls itself inside its own definition (return statement calls the factorial function). In this case, the factorial function executes until the value of n equals 0.![]()
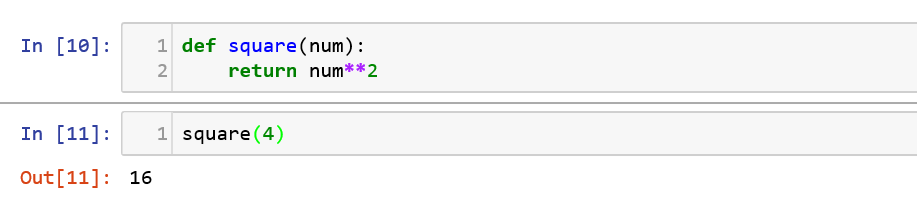
Lambda
These expressions allow us to create “anonymous” functions that are similar to the standard function definition. It is considered to be one of the most useful tools in Python since it allows us to create ad-hoc functions. For eg, let us take a square function declaration:![]()
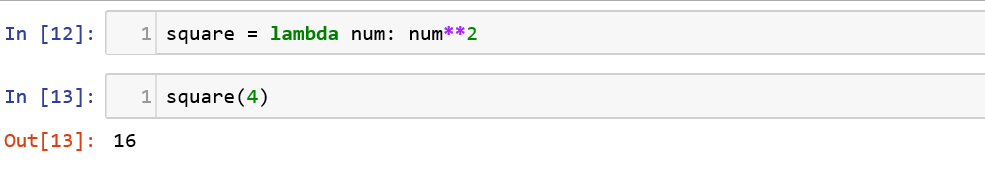
Now, let us re-write the same function using lambda expression:![]()
Let us try to reverse a string input provided using lambda definition. This will give us a better understanding of its versatility.
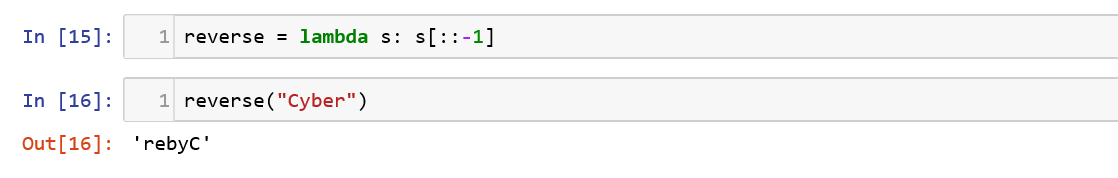
lambda expressions are used widely along with with map(), filter() and reduce() functions.
Numbers and Operators
In Python, we predominantly use two types of numbers which is Integers (positive and negative) and Floating Point numbers.
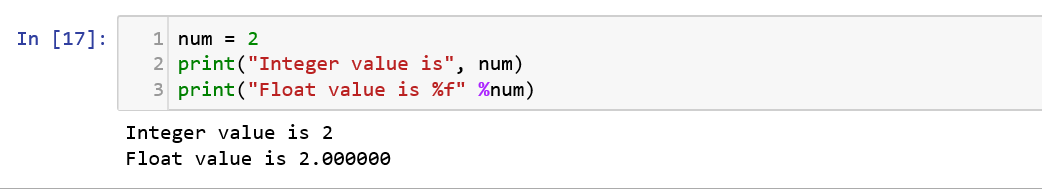
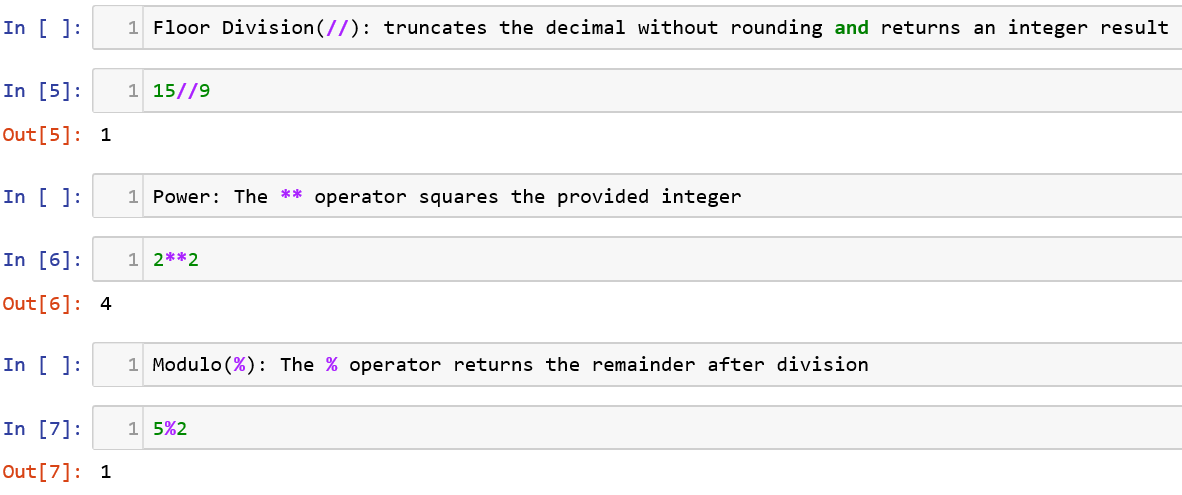
We are all familiar with the basic arithmetic operators (+,-,*,/) so let us dive into the other type of operators that can be used.
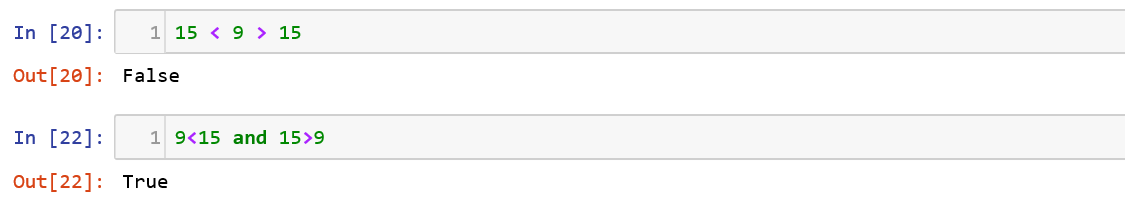
The comparison operators that are available for manipulation are “==”, “!=”, “<>”, “≤”, “≥”, “>” and “<”. You can do a multiple comparisons in a single line using Boolean operators.![]()
Loops and Statements
All the basic loop structures like for, while, nested loops and if, elif and else statements, that you would find in any programming language, are available in Python as well.
For loop
The loop iterates over the items in order, executing the entire code block each time. We can use the range() function to specify the number of times we want the for loop to execute.![]()
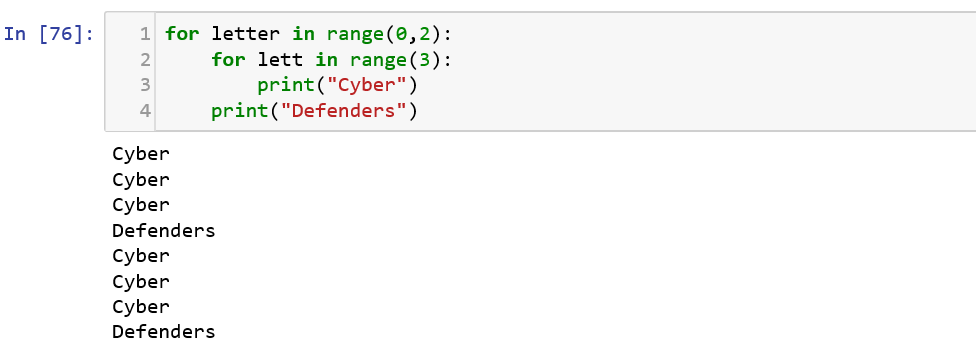
We can also specify the values to be evaluated in a for loop directly instead of range().![]()
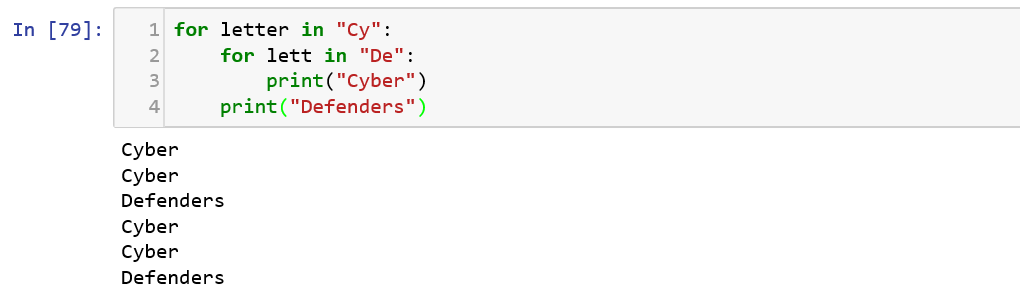
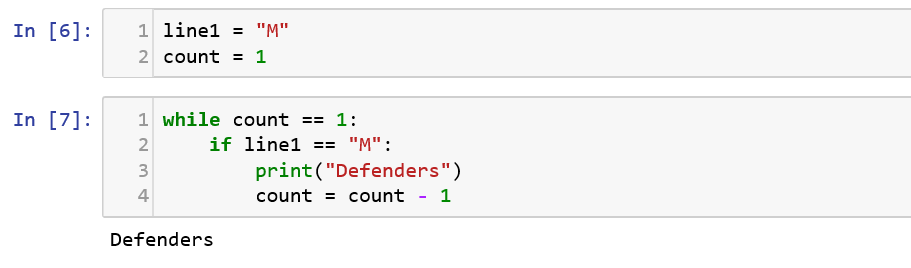
While loop
Similar to the for loop, let us see how the while loop functions. According the below function, the loop will execute until the count value is 1.
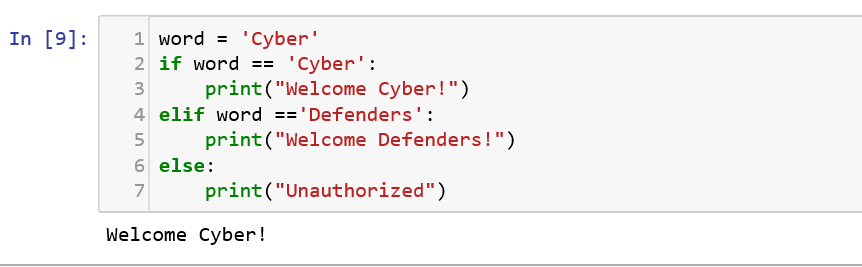
If.. Elif.. Else statement
These statements in Python allows us to tell the computer to take alternative course of actions based on a certain set of results. Let us look at a simple example:
String functions
Python offers a variety of functions that can be done on a string object that eases the pain of printing the desired output. We can perform the basic string functions like upper(), lower() and capitalize() for upper case, lower case and sentence case respectively. Let us see some other interesting functions that are available to manipulate a string:
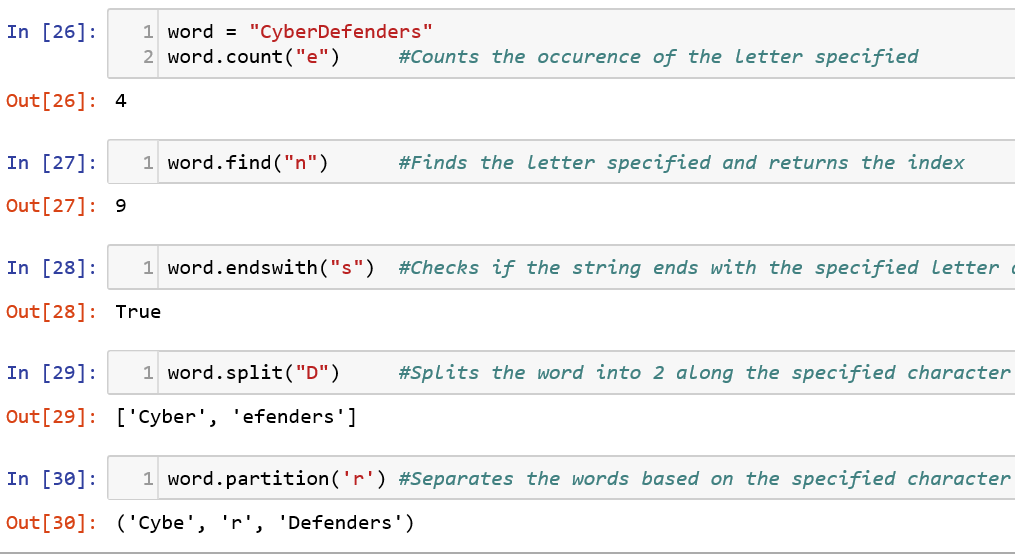
To check if the string is in some case, you can use the is<check>() methods like isalpha(), isspace(), isalnum(), islower() and isupper().
File functions
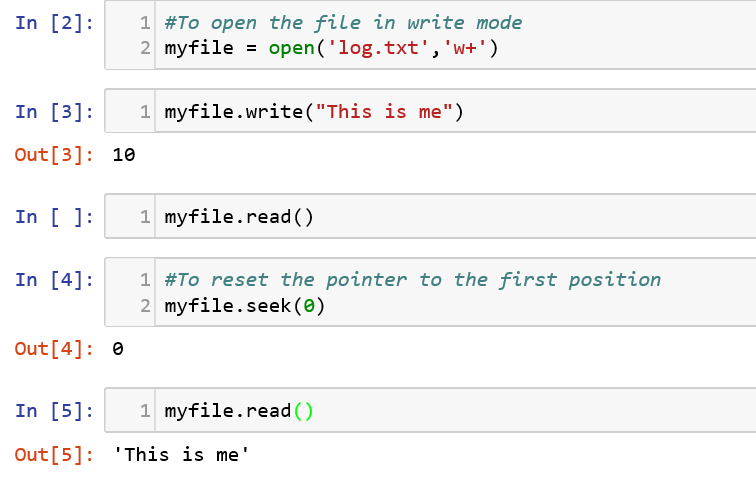
File objects can be used by Python to interact with the files in your computer. In order to understand this, let us see now see first open a file in write mode, write a line to it and try to read the file.
Data Structures in Python
Data Structures in any programming language are used to store and retrieve information, which also defines the relationship between the data and operations that are authorized to be performed on that data. There are two types:
Primitive (Integer, Boolean, Float, Strings)
Non-Primitive (Arrays, Tuples, Lists, Dictionaries, Sets, Files)
We have already discussed the primitive data structures above so let’s move on to the non-primitive ones. Of all the aforementioned, Lists and Dictionaries are the most popular ones to be used by the developers.
Lists
A list holds an ordered collection of items which can be strings, integers, etc. The items need to be closed in “[]” square braces to indicate that the group of items needs to be treated as a list. Let us try to understand the data structure and the various methods used with it.![]()
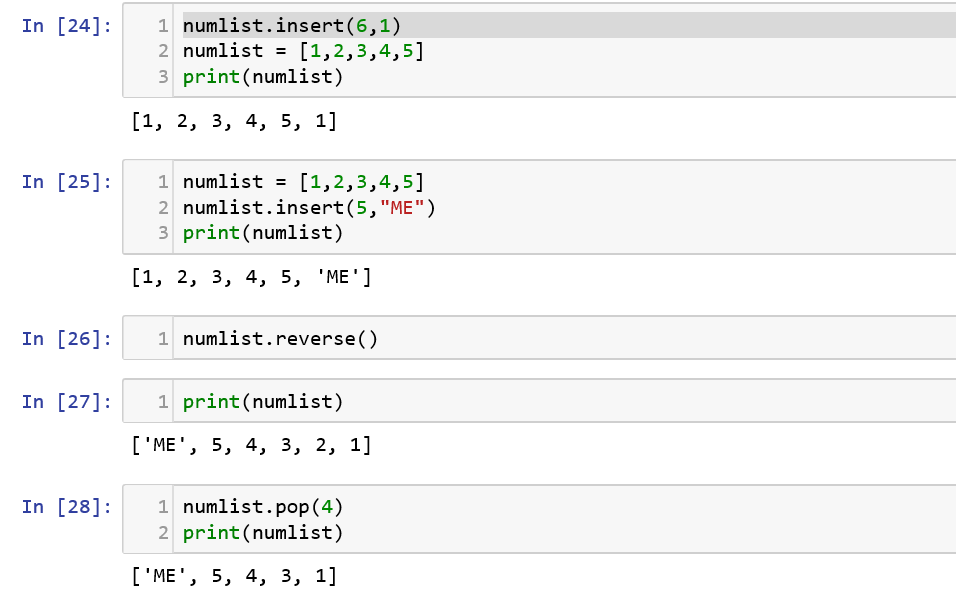
When we type the name of the list with a ‘.’ in the end and press the TAB key, we will be able to see the various methods that can be used on the list which includes append(), count(), reverse(), extend(), insert(), pop(), remove() and sort(). Let us see a few of them and their functioning through the code sample:
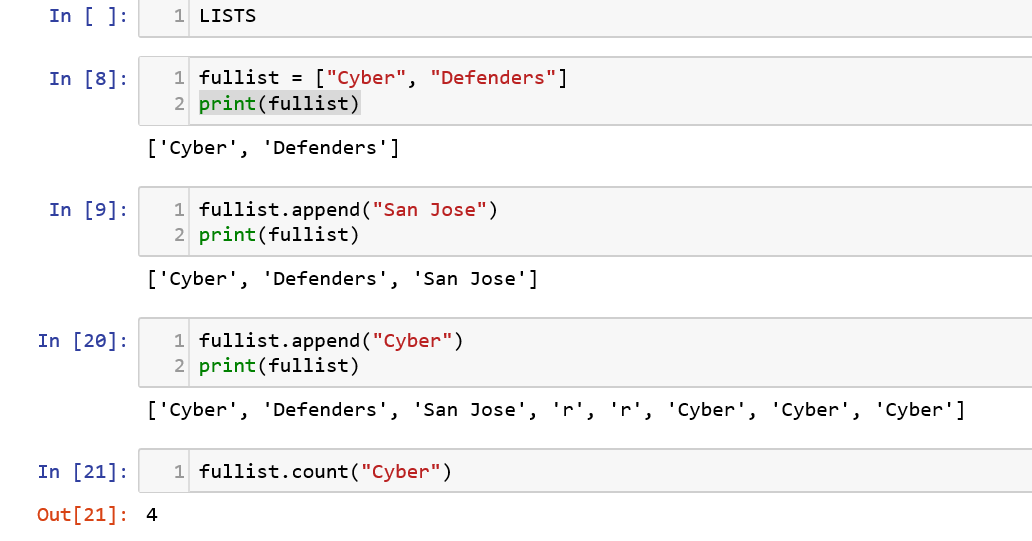
Arrays
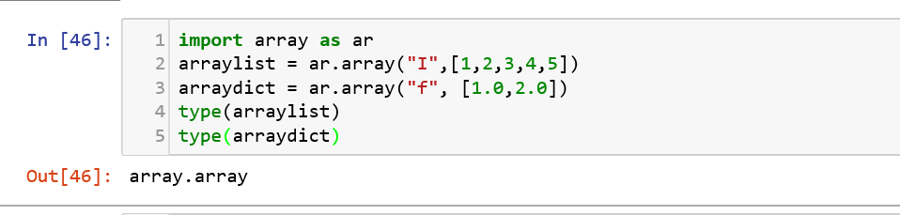
In Python, arrays are not so popular as lists when compared to their use in other programming languages. The prime difference between them is that all the elements in an array need to be of the same datatype. Arrays are declared using the array module, which needs to be imported before initializing them. The data type of the array has to be specified during the array creation.![]()
Dictionaries
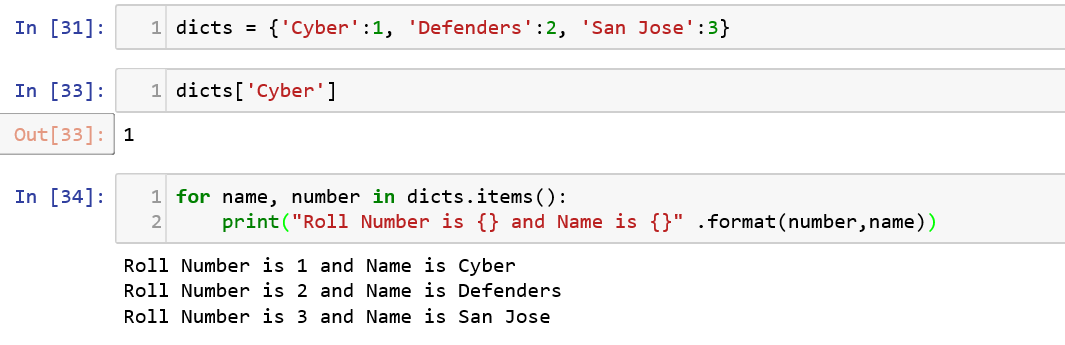
Dictionaries are made of key-value pairs, where key is used to identify the item and the value holds the value of the item. Let us see how to declare a dictionary say “dicts” and try to iterate through each item using the items() function.
Tuples
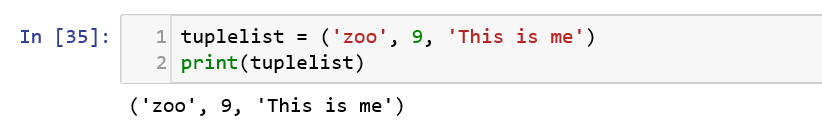
Tuples look similar to lists except for the declaration in “( )” instead of “[ ]”. They are used to hold together objects that are immutable, in simple terms, the values cannot be modified.
Regular Expressions
Regular expressions are used for finding matching patterns of text which works with a formal syntax. It is shortly known as REGEX. It is predominantly used in solving parsing problems. Let us see a code sample that can be used to determine the strength of a password depending on the constraints matching the regex pattern.
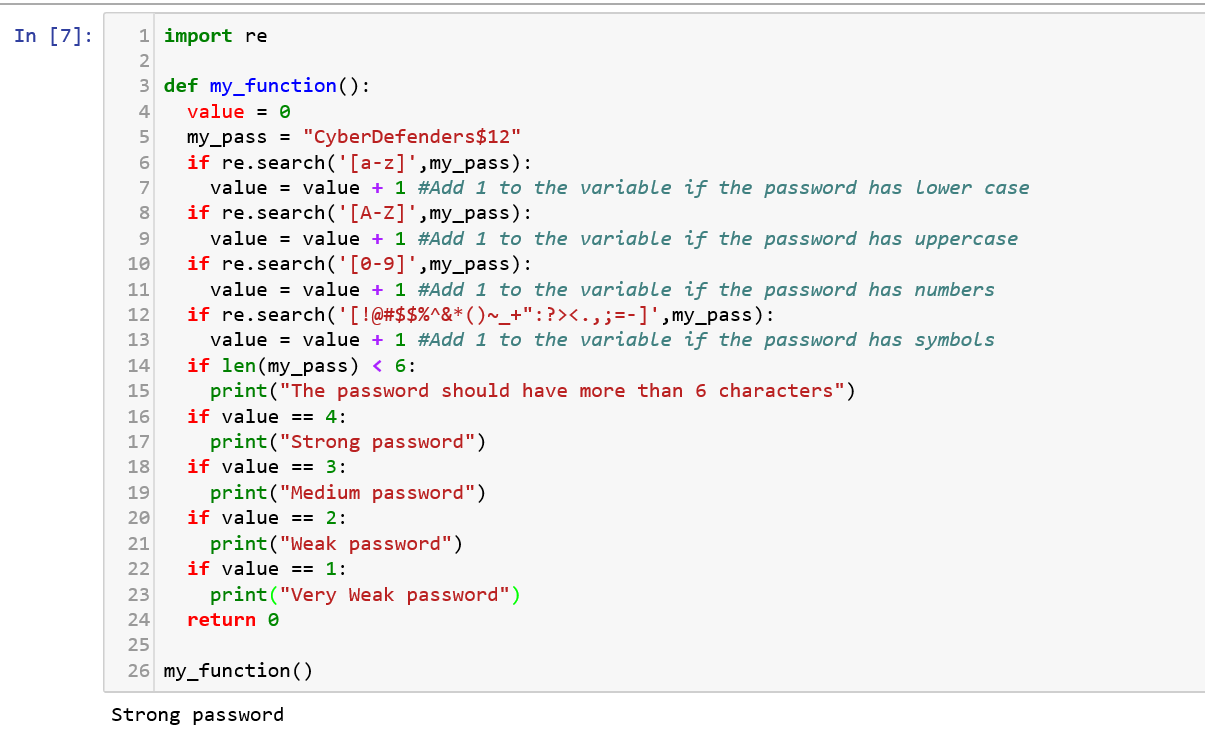
As you can see, re.search() function is used to search for matching strings, which is then compared with the input string my_pass. The other functions that are commonly used with regex are compile(), findall() and match().
With this, we end our first lesson in our path towards learning Python for Cyber Security.
Watch out for the next post soon!
Happy Learning!!
Practice Problems
Simulate the basic calculator function in a simple python program and obtain user input to perform the arithmetic operations
Obtain user input and try to display the calendar for that month
Get a sentence from the user and sort the words in alphabetical order
Additional resources to learn:
Cybrary Course: Python for Cyber Security Professionals — https://www.cybrary.it/course/python/
Automate the Boring Stuff Online Book — https://automatetheboringstuff.com/
Cracking the Code with Python Online Book — https://inventwithpython.com/cracking/
The Anti-Textbook: Learn Python by Doing — https://github.com/thewhitetulip/build-app-with-python-antitextbook
Byte size Python — http://www.pythonbytesize.com/video-list-website.html
Interactive Python Online Book — http://interactivepython.org/runestone/static/thinkcspy/index.html
Functional Introduction to Python Online Book — https://github.com/noahgift/functional_intro_to_python
For Coding Practice: https://projecteuler.net/ http://codingbat.com/python
Last updated